 |
HP OpenVMS System Services Reference Manual
If the handle specified is zero, a new system
notification request object is created, and a handle for the new object
is returned.
If the event specified is non-zero, that event is
added to the set of events which trigger notification on the
notification object.
The service will verify that the input parameters specify a valid
request and enable the object for notification. Notification is
accomplished by AST delivery. After the AST has been delivered,
notification must again be enable on the object before another
notification (AST delivery) can occur if flag is not
set.
Errors are returned in the following cases:
- If quotas are exceeded, an error is returned. It is important to
note that this routine returns an error and will not retry an attempt
to get quota if quota is exhausted on the first attempt.
- See the Condition Values Returned section for types of errors that
can be returned.
- If the astadr argument is omitted, and a new
notification object is being created, SS$_BADPARAM is returned.
- If the event argument is incorrectly specified,
SS$_BADPARAM is returned.
- If the access mode parameter is more privileged than the mode of
the caller, the mode of the caller is used.
- If specified, the handle argument must be
writeable from the mode of the caller. SS$_ACCVIO is returned if this
is not the case.
Required Access or Privileges
None
Required Quota
ASTLM
Related Services
$CLEAR_SYSTEM_EVENT
Condition Values Returned
|
SS$_NORMAL
|
The service completed successfully.
|
|
SS$_ACCVIO
|
The service cannot access the locations specified by one or more
arguments.
|
|
SS$_BADPARAM
|
One of more arguments has an invalid value.
|
|
SS$_EXASTLM
|
The process exceeded its quota for outstanding ASTs.
|
|
SS$_INSFMEM
|
The system dynamic memory is insufficient to complete the service.
|
$SET_UNWIND_TABLE (I64 Only)
Registers or extends unwind table (UT) information.
Format
SYS$SET_UNWIND_TABLE code_base_va, code_size, ut_base_va, ut_size,
gp_value, unwind_info_base, name
C Prototype
ind SYS$SET_UNWIND_TABLE (unsigned __int64 code_base_va, unsigned
__int64 code_size, unsigned __int64 ut_base_va, unsigned __int64
ut_size, unsigned __int64 gp_value, unsigned __int64 unwind_info_base,
void *name);
Arguments
code_base_va
| OpenVMS usage: |
address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
With code_size, defines the potential code range.
code_base_va is required for both creation and
extension calls. code_base_va is the process virtual
address of the start of the code region. code_size is
the size of the code region in bytes. An error is returned if this
overlaps any existing range.
code_size
| OpenVMS usage: |
address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
With code_base_va, defines the potential code range.
code_base_va is required for both creation and
extension calls. code_base_va is the process virtual
address of the start of the code region. code_size is
the size of the code region in bytes. An error is returned if this
overlaps any existing range.
ut_base_va
| OpenVMS usage: |
address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
With ut_size, describes the unwind table (UT).
ut_base_va is the process virtual address of the UT
and must be quadword aligned. ut_size is the size of
the UT in bytes and must be a multiple of the size (24 bytes: 3
quadwords) of an unwind table entry (UTE). The UTEs must describe
nonoverlapping code subregions within the overall code region.
ut_size
| OpenVMS usage: |
address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
With ut_base_va, describes the unwind table (UT).
ut_base_va is the process virtual address of the UT
and must be quadword aligned. ut_size is the size of
the UT in bytes and must be a multiple of the size (24 bytes: 3
quadwords) of an unwind table entry (UTE). The UTEs must describe
nonoverlapping code sub regions within the overall code region.
gp_value
| OpenVMS usage: |
address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Ignored on extension calls, required on create calls. The Global Data
Pointer (GP) value for the routines described by these unwind tables.
unwind_info_base
| OpenVMS usage: |
address |
| type: |
quadword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Ignored on extension calls; required on create calls. The
unwind_info_base plus a particular UTE UIB offset must
add up to the process virtual address of that UIB. Typically for static
code (activated images from disk), this specifies the process virtual
base address of the segment containing the UIBs. However, dynamically
generated code, for example, can pass a zero for the
unwind_info_base and have the full process virtual
addresses of the UIBs in their UTEs.
name
| OpenVMS usage: |
pseudo-image-name |
| type: |
character-code-text-string |
| access: |
read only |
| mechanism: |
by descriptor-fixed-length string descriptor |
Passed by descriptor (ignored on extension calls). May be used for
traceback. Need not be unique. Should be less than 255 characters (will
be truncated, otherwise).
Description
This interface can be used to register or extend unwind information. It
is expected, for example, that applications that dynamically create
code will also need to dynamically create unwind tables (UTs) and
unwind information blocks (UIBs) for that code. This interface
registers such information with the operating system.
The image activator also uses this interface to register unwind
information for shareable and main images. Note that the code region,
though fully specified in terms of its potential size, need not be full
of actual code at its initial registration. The unwind table, however,
must describe all the code that could execute within that region and
that needs unwind information, at any given time. Note also that the
unwind table entries (UTEs) within a registered unwind table must
remain sorted (ascending order) at any given time.
To create a new registration, specify a new (not registered) code
range. On a creation, all parameters (except name)
must be specified.
To extend an existing registration, specify an existing (registered)
code_base_va. On extension, only the identifying
code_base_va and new UT range need be specified, that is, the other
parameters may be zeros. An extension call can only alter that
registration's ut_base_va and ut_size.
The creator caller's mode defines the mode from which the registration
may be extended or removed.
Failure status is returned on creation if the input code range overlaps
an already existing range.
Required Access or Privileges
Unwind table information that describes code in process space can be
registered from any mode.
Unwind table information that describes code in system space can be
registered only from kernel mode or executive mode.
Required Quota
None
Related Services
SYS$CLEAR_UNWIND_TABLE, SYS$GET_UNWIND_ENTRY_INFO. Also refer to
LIB$GET_UIB_INFO in HP OpenVMS Calling Standard.
Condition Values Returned
|
SS$_NORMAL
|
Routine completed successfully.
|
|
SS$_BADPARAM
|
Missing or illegal parameter.
|
|
SS$_VA_IN_USE
|
Overlap detected.
|
|
SS$_ACCVIO
|
Name descriptor cannot be read.
|
$SHOW_INTRUSION
Searches for and returns information about records in the intrusion
database matching the caller's specifications.
Format
SYS$SHOW_INTRUSION user_criteria ,intruder ,intruder_len ,breakin_block
,[flags] ,[context]
C Prototype
int sys$show_intrusion (void *user_criteria, void *intruder, unsigned
short int *intruder_len, void *breakin_block, unsigned int flags,
unsigned int *context);
Arguments
user_criteria
| OpenVMS usage: |
char_string or item_list_3 |
| type: |
character-coded text string or longword
(unsigned) |
| access: |
read only |
| mechanism: |
by descriptor--fixed-length string descriptor or by
reference |
If the CIA$M_ITEMLIST flag is FALSE:
The user_criteria argument is the description of
intruder or suspect. The user_criteria argument is the
address of a character-string descriptor pointing to a buffer
containing the user criteria to match an intrusion record's user
specification in the intrusion database.
The user_criteria argument is a character string of
between 1 and 1058 bytes containing characters to match the user
specification on records in the intrusion database.
A user specification is any combination of the suspect's or intruder's
source node name, source user name, source DECnet for OpenVMS address,
local failed user name, local terminal, or the string UNKNOWN. The user
specification for an intrusion record is based on the input to the
$SCAN_INTRUSION service and the settings of the LGI system parameter.
For more information, refer to the HP OpenVMS Guide to System Security.
Wildcards are allowed for the user_criteria argument.
For more information about using wildcards to scan the intrusion
database, see the Description section.
If the CIA$M_ITEMLIST flag is TRUE:
The user_criteria argument is now the address of an
32-bit item list. If the item list is used, one item, the
CIA$_USER_CRITERIAL item, must be present in the item list.
The following table lists the valid item descriptions for the
user_criteria argument:
| Item |
Description |
|
CIA$_OUTPUT_LIST
|
Address of an 8192-byte buffer into which the service writes the
associated node information for the returned intrusion record.
|
|
CIA$_SCSNODE_LIST
|
Address of a list of 8-character null-padded SCS nodenames for which
the caller wants to see intrusion information about.
|
|
CIA$_USER_CRITERIAL
|
Address of a buffer, 1-1058 bytes long, containing the intruder or
suspect.
|
If a CIA$_SCSNODE_LIST item is provided, an intrusion record will only
be returned if it originated on one of the nodes specified. If a
CIA$_SCSNODE_LIST item is not provided, records from all nodes will be
candidates for display. Multiple CIA$_SCSNODE_LIST items are permitted
in the item list.
If a CIA$_OUTPUT_LIST item is provided, the item is filled with
node-count records on return. The returned intrusion record will have a
breakin block with a valid attempt-count field. The node-count records
will have the name and attempt-count for each node represented.
intruder
| OpenVMS usage: |
char_string |
| type: |
character-coded text string |
| access: |
write only |
| mechanism: |
by descriptor--fixed-length string descriptor |
User specification of the matched intruder or suspect record in the
intrusion database. The intruder argument is the
address of a character-string descriptor pointing to a buffer to
receive the user specification of the matched record in the intrusion
database.
The intruder argument is a 1058-byte string that will
receive the user specification of a record in the intrusion database
that matches the specifications in the user_criteria
and flags arguments.
intruder_len
| OpenVMS usage: |
string length |
| type: |
longword (unsigned) |
| access: |
write only |
| mechanism: |
by reference |
Length of returned string in the intrusion buffer. The
intruder_len argument is the address of a longword to
receive the length of the returned intrusion buffer.
The possible range of the intruder_len argument is 0
to 1058 bytes. If the longword specified by the argument contains a 0
after the call to the service, either the service did not find a record
that matched the user criteria in the intrusion database, or there are
no more matching items in the intrusion database.
breakin_block
| OpenVMS usage: |
record |
| type: |
block of 2 longwords (unsigned) and 1 quadword
(unsigned) |
| access: |
write only |
| mechanism: |
by reference |
Block to receive various information in the intrusion database about a
record matching the user criteria. The breakin_block
argument is the address of a structure with the following format:
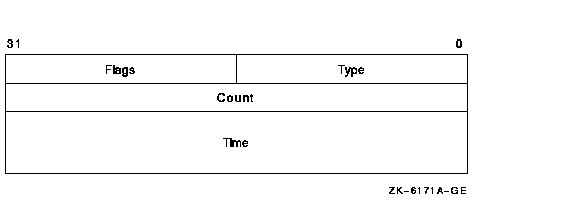
The following table defines the break-in block fields:
| Field |
Description |
|
Type
|
Unsigned longword containing two pieces of information: the types of
the matched record and the status of the suspect---SUSPECT or INTRUDER.
The possible values for the record type are TERM_USER, TERMINAL,
USERNAME, and NETWORK. The possible values for the status are SUSPECT
or INTRUDER. These constants are defined in $CIADEF in STARLET.
The implication is that each type will have two bits set: one bit
represents the status, and the other bit represents the record type.
|
|
Count
|
Unsigned longword containing the number of login failures or break-in
attempts made by the specified intruder or suspect.
|
|
Time
|
Quadword time format indicating the time when the record will expire.
|
flags
| OpenVMS usage: |
mask_longword |
| type: |
longword (unsigned) |
| access: |
read only |
| mechanism: |
by value |
Type of records in the intrusion database about which information is to
be returned. The flags argument is a longword bit mask
wherein each bit corresponds to an option.
Each option has a symbolic name. The $CIADEF macro defines the
following valid names:
| Symbolic Name |
Description |
|
CIA$M_ALL
|
All records will be shown. If the
flags argument is omitted, this value is assumed.
|
|
CIA$M_INTRUDERS
|
Only intruder records matching the criteria specified by the
user_criteria argument will be returned. The value of
the flag field in the break-in block will always be 1.
|
|
CIA$M_ITEMLIST
|
If FALSE, the
user_criteria argument is a character string. If TRUE,
this argument is a 32-bit item list.
|
|
CIA$M_SUSPECTS
|
Only suspect records matching the criteria specified by the
user_criteria argument will be returned. The value of
the flag field in the break-in block will always be 0.
|
Each of these options is mutually exclusive.
context
| OpenVMS usage: |
context |
| type: |
longword (unsigned) |
| access: |
write only |
| mechanism: |
by reference |
Context information to keep between related calls to the
$SHOW_INTRUSION service. The context argument is the
address of a longword that receives a context from the service.
The initial value contained in the unsigned longword pointed to by the
context argument must be 0. The contents of the
unsigned longword must not be changed after the service has set its
value. If the contents of the context argument are
changed between calls to the service, SS$_BADCONTEXT will be returned.
Contexts become invalid after one-half hour of non-use. This means that
if you call the $SHOW_INTRUSION service with a wildcard in the
user_criteria argument and do not call the service to
get the next matching record within one-half hour, the context becomes
invalid. If the context has become invalid, you must restart your
search of the intrusion database from the beginning by resetting the
context to 0.
Description
The Show Intrusion service returns information about records in the
intrusion database that match the criteria you specify.
You can retrieve information about multiple records in the intrusion
database by specifying wildcards for the user_criteria
argument. For example, specifying an asterisk (*) for the
user_criteria argument and CIA$M_ALL_RECORDS for the
flags argument will return information about all
records in the database. Specifying TTA4* for the
user_criteria argument and CIA$M_SUSPECTS_ONLY for the
flags argument will return information about all
suspects who have had failures on terminal TTA4.
If you specify a wildcard string for the user_criteria
argument, you must also include a context argument.
Because the service can only return information about one intrusion
record at a time, you must call the service repeatedly to retrieve
information about more than one record. The service will return
SS$_NOMOREITEMS when information about all of the matching records has
been returned. No intrusion information is returned from the call that
returns SS$_NOMOREITEMS.
Required Access or Privileges
SECURITY privilege is required.
Required Quota
None
Related Services
$DELETE_INTRUSION, $SCAN_INTRUSION
Condition Values Returned
|
SS$_NORMAL
|
The service completed successfully.
|
|
SS$_ACCVIO
|
The
user_criteria or
context argument cannot be read, or the
intruder,
intruder_len,
breakin_block, or
context argument cannot be written.
|
|
SS$_BADBUFLEN
|
The length of one of the specified arguments is out of range.
|
|
SS$_BADCONTEXT
|
The
context argument did not contain a 0 on the first call
to the service. The
context argument's value changed between consecutive
calls to the service.
|
|
SS$_BADPARAM
|
An invalid value was specified in the
flags argument, or mutually exclusive options were
specified in the
flags argument.
|
|
SS$_NOMOREITEMS
|
All items matching the specified criteria have been returned.
|
|
SS$_NOSECURITY
|
The caller does not have SECURITY privilege.
|
|
|
|
|
This service can also return any of the following messages passed from
the security server:
|
|
SECSRV$_NOSUCHINTRUDER
|
No records matching the specified criteria were found in the intrusion
database.
|
|
SECSRV$_SERVERNOTACTIVE
|
The security server is not currently active. Try the request again
later.
|
|
