Software > OpenVMS Systems > Documentation > 82final > 6048 HP OpenVMS Systems Documentation |
HP OpenVMS System Management Utilities Reference Manual
Appendix E
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Field | Meaning |
|---|---|
| USG$L_SERIALNUM | Serial number of the volume. This is an octal longword value. |
| USG$T_STRUCNAM | Volume set name (if the volume is part of a volume set). For a Files-11 Structure Level 1 volume, this field contains binary zeros; for a Files-11 Structure Level 2 or 5 volume that is not part of a volume set, this field contains spaces. The length of this field is USG$S_STRUCNAME. |
| USG$T_VOLNAME | Volume name of relative volume 1. The length of this field is USG$S_VOLNAME. |
| USG$T_OWNERNAME | Volume owner name. The length of this field is USG$S_OWNERNAME. |
| USG$T_FORMAT | Volume format type. For a Files-11 Structure Level 1 volume, this field contains "DECFILE11A"; for a Files-11 Structure Level 2 or 5 volume, this field contains "DECFILE11B". The length of this field is USG$S_FORMAT. |
| USG$Q_TIME | Quadword system time when this usage file was created. The length of this field is USG$S_TIME. |
Each file summary record is characterized by the type code USG$K_FILE in the USG$B_TYPE field of the record. Table E-2 contains a description of all the fields in these records.
| Field | Meaning |
|---|---|
| USG$L_FILEOWNER | File owner UIC. This can be considered as a single longword value or as two word values (USG$W_UICMEMBER and USG$W_UICGROUP). |
| USG$W_UICMEMBER | The member field of the file owner UIC. This is an octal word value. |
| USG$W_UICGROUP | The group field of the file owner UIC. This is an octal word value. |
| USG$L_ALLOCATED | Number of blocks allocated to the file, including file headers. This is a decimal longword value. |
| USG$L_USED | Number of blocks used, up to and including the end-of-file block. This is a decimal longword value. |
| USG$W_DIR_LEN | Length of the directory string portion of USG$T_FILESPEC, including the brackets. This is a decimal word value. |
| USG$W_SPEC_LEN | Length of the complete file specification in USG$T_FILESPEC. This is a decimal word value. |
| USG$T_FILESPEC |
File specification, in the following format:
[dir]nam.typ;ver This field is of variable length. A file that has more than one directory entry is listed under the first file specification found. A lost file has an empty directory string "[]" and the file name is taken from the file header. In some cases this information does not exist; you must take this into consideration when you write application programs to process the usage file. The length of this field is USG$S_FILESPEC. |
The symbolic names referenced in both the identification and the file summary records are defined in the system definition macro $USGDEF. The length of the identification record is USG$K_IDENT_LEN. The length of a file summary record is USG$K_FILE_LEN.
This appendix describes the format of the auditing messages written to the security auditing log file. The default audit log file SECURITY.AUDIT$JOURNAL is created by default in the SYS$COMMON:[SYSMGR] directory.
Each security audit record consists of a header packet followed by one or more data packets, as shown in Figure F-1. The number of data packets depends on the type of information being sent. This appendix describes the format of the audit header and its data packets as well as the contents of the data packets.
Figure F-1 Format of a Security Audit Message
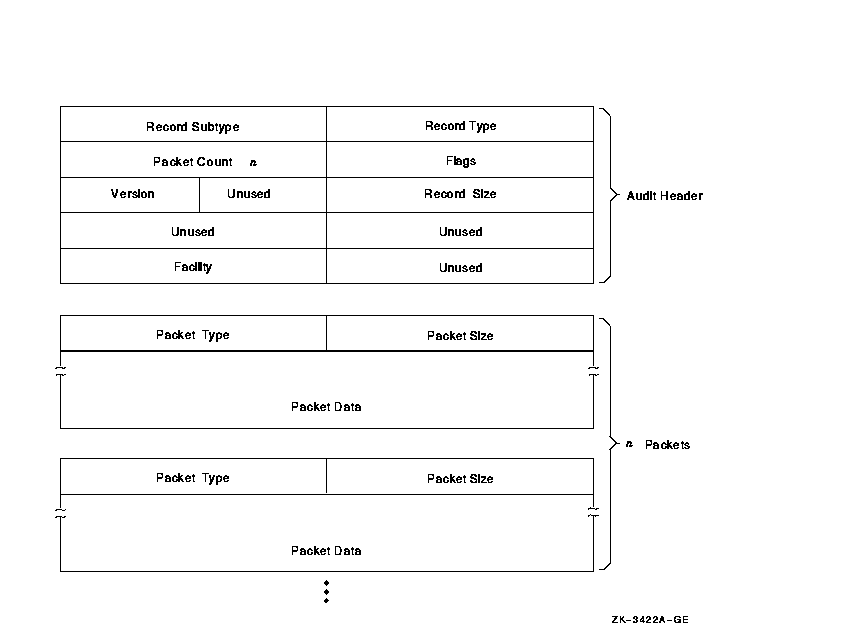
Figure F-2 Audit Header Packet Format
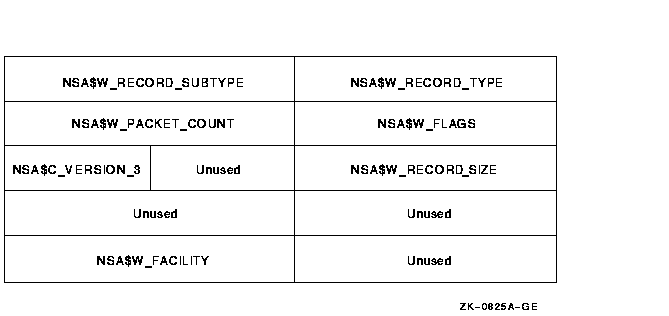
| Field | Symbolic Offset | Contents |
|---|---|---|
| Type | NSA$W_RECORD_TYPE | Indicates the type of event that has occurred. See Table F-2 for details. |
| Subtype | NSA$W_RECORD_SUBTYPE | Further defines the type of event that has occurred. See Table F-2 for details. |
| Flags | NSA$W_FLAGS | Identifies any flags associated with the audited event. See Table F-3 for details. Reserved to HP. (Word) |
| Packet count | NSA$W_PACKET_COUNT | Number of data packets in the audit record. (Word) |
| Record size | NSA$W_RECORD_SIZE | Total size of the audit message; the size represents the header packet plus all its data packets. (Word) |
| Version | NSA$C_VERSION_3 | Indicates the version of the security auditing facility. The symbol NSA$C_VERSION_3 indicates the current version. (Byte) |
| Facility | NSA$W_FACILITY | The facility code for the generated event. By default, this field is zero, indicating a system-generated event. (Word) |
When you enter subtypes, do not include a prefix, as shown in Table F-2.
Symbols representing the types or subtypes of security events are listed in Table F-2. For each audit event record type defined by NSA$W_RECORD_TYPE, there is a record subtype defined by the symbol NSA$W_RECORD_SUBTYPE, which further defines the event.
| Symbols for Event Types and Subtypes | Meaning | |
|---|---|---|
| NSA$C_MSG_AUDIT | Systemwide change to auditing | |
| ALARM_STATE | Events enabled as alarms | |
| AUDIT_DISABLED | Audit events disabled | |
| AUDIT_ENABLED | Audit events enabled | |
| AUDIT_INITIATE | Audit server startup | |
| AUDIT_LOG_FIRST | First entry in audit log (backward link) | |
| AUDIT_LOG_FINAL | Final entry in audit log (forward link) | |
| AUDIT_STATE | Events enabled as audits | |
| AUDIT_TERMINATE | Audit server shutdown | |
| SNAPSHOT_ABORT 1 | System snapshot attempt has aborted | |
| SNAPSHOT_ACCESS 1 | Snapshot file access/deaccess | |
| SNAPSHOT_SAVE 1 | System snapshot save in progress | |
| SNAPSHOT_STARTUP 1 | System booted from a snapshot file | |
| NSA$C_MSG_BREAKIN | Break-in attempt detected | |
| BATCH | Batch process | |
| DETACHED | Detached process | |
| DIALUP | Dialup interactive process | |
| LOCAL | Local interactive process | |
| NETWORK | Network server task | |
| REMOTE | Interactive process from another network node | |
| SUBPROCESS | Subprocess | |
| NSA$C_MSG_CONNECTION | Logical link connection or termination | |
| CNX_ABORT | Connection aborted | |
| CNX_ACCEPT | Connection accepted | |
| CNX_DECNET_CREATE | DECnet logical link created | |
| CNX_DECNET_DELETE | DECnet logical link disconnected | |
| CNX_DISCONNECT | Connection disconnected | |
| CNX_INC_ABORT | Incoming connection request aborted | |
| CNX_INC_ACCEPT | Incoming connection request accepted | |
| CNX_INC_DISCONNECT | Incoming connection disconnected | |
| CNX_INC_REJECT | Incoming connection request rejected | |
| CNX_INC_REQUEST | Incoming connection request | |
| CNX_IPC_CLOSE | Interprocess communication association closed | |
| CNX_IPC_OPEN | Interprocess communication association opened | |
| CNX_REJECT | Connection rejected | |
| CNX_REQUEST | Connection requested | |
| NSA$C_MSG_INSTALL | Use of the Install utility (INSTALL) | |
| INSTALL_ADD | Known image installed | |
| INSTALL_REMOVE | Known image deleted | |
| NSA$C_MSG_LOGFAIL | Login failure | |
|
See subtypes for
NSA$C_MSG_BREAKIN |
||
| NSA$C_MSG_LOGIN | Successful login | |
|
See subtypes for
NSA$C_MSG_BREAKIN |
||
| NSA$C_MSG_LOGOUT | Successful logout | |
|
See subtypes for
NSA$C_MSG_BREAKIN |
||
| NSA$C_MSG_MOUNT | Volume mount or dismount | |
| VOL_DISMOUNT | Volume dismount | |
| VOL_MOUNT | Volume mount | |
| NSA$C_MSG_NCP | Modification to network configuration database | |
| NCP_COMMAND | Network Control Program (NCP) command issued | |
| NSA$C_MSG_NETPROXY | Modification to network proxy database | |
| NETPROXY_ADD | Record added to network proxy authorization file | |
| NETPROXY_DELETE | Record removed from network proxy authorization file | |
| NETPROXY_MODIFY | Record modified in network proxy authorization file | |
| NSA$C_MSG_OBJ_ACCESS | Object access attempted | |
| OBJ_ACCESS | Access attempted to create, delete, or deaccess an object | |
| NSA$C_MSG_OBJ_CREATE | Object creation attempted | |
| OBJ_CREATE | Access attempted to create an object | |
| NSA$C_MSG_OBJ_DEACCESS | Object deaccessed | |
| OBJ_DEACCESS | Attempt to complete access to an object | |
| NSA$C_MSG_OBJ_DELETE | Object deletion attempted | |
| OBJ_DELETE | Object deletion attempted | |
| NSA$C_MSG_PROCESS | Process controlled through a system service | |
| PRC_CANWAK | Process wakeup canceled | |
| PRC_CREPRC | Process created | |
| PRC_DELPRC | Process deleted | |
| PRC_FORCEX | Process exit forced | |
| PRC_GETJPI | Process information gathered | |
| PRC_GRANTID | Process identifier granted | |
| PRC_RESUME | Process resumed | |
| PRC_REVOKID | Process identifier revoked | |
| PRC_SCHDWK | Process wakeup scheduled | |
| PRC_SETPRI | Process priority altered | |
| PRC_SIGPRC | Process exception issued | |
| PRC_SUSPND | Process suspended | |
| PRC_TERM | Process termination notification requested | |
| PRC_WAKE | Process wakeup issued | |
| NSA$C_MSG_PRVAUD | Use of privilege | |
| PRVAUD_FAILURE | Unsuccessful use of privilege | |
| PRVAUD_SUCCESS | Successful use of privilege | |
| NSA$C_MSG_RIGHTSDB | Modification to the rights database | |
| RDB_ADD_ID | Identifier added to rights database | |
| RDB_CREATE | Rights database created | |
| RDB_GRANT_ID | Identifier granted to user | |
| RDB_MOD_HOLDER | List of identifier holders modified | |
| RDB_MOD_ID | Identifier name or attributes modified | |
| RDB_REM_ID | Identifier removed from rights database | |
| RDB_REVOKE_ID | Identifier taken away from user | |
| NSA$C_MSG_SYSGEN | Use of the System Generation utility (SYSGEN) | |
| SYSGEN_SET | System parameter modified | |
| NSA$C_MSG_SYSTIME | Modification to system time | |
| SYSTIM_SET | System time set | |
| SYSTIM_CAL | System time calibrated | |
| NSA$C_MSG_SYSUAF | Modification to system user authorization file (SYSUAF) | |
| SYSUAF_ADD | Record added to system user authorization file | |
| SYSUAF_COPY | Record added to system user authorization file | |
| SYSUAF_DELETE | Record deleted from system user authorization file | |
| SYSUAF_MODIFY | Record modified in system user authorization file | |
| SYSUAF_RENAME | Record renamed in system user authorization file | |
Table F-3 identifies any flags associated with the audited event.
The symbol NSA$K_MSG_HDR_LENGTH defines the current size of the message header (in bytes).
| Symbol | Meaning |
|---|---|
| NSA$M_ACL | Event generated by an alarm access control entry (ACE) or an audit ACE. |
| NSA$M_ALARM | Event is a security alarm. |
| NSA$M_AUDIT | Event is a security audit. |
| NSA$M_FLUSH | Event forced the audit server to write all buffered event messages to the audit log file. |
| NSA$M_FOREIGN | Event occurred outside of the system trusted computing base. |
| NSA$M_MANDATORY | Event resulted from a mandatory process audit. |
| Previous | Next | Contents | Index |