Software > OpenVMS Systems > Documentation > 82final > 6553 HP OpenVMS Systems |
HP Advanced Server for OpenVMS
|
| Previous | Contents | Index |
The Advanced Server builds security into the operating system, thereby enabling efficient management of large networks. You can set up domains and trust relationships between domains to centralize user accounts and other security information, making the network easier to manage and use. Every user needs only one account. This account can provide the user with access to resources anywhere on the network.
The Advanced Server also incorporates enhanced features that provide you with a high level of control over user and resource permissions and auditing. These features include support of:
Optionally, the Advanced Server accommodates both the Advanced Server and OpenVMS security models.
For more information about how the Advanced Server integrates network security and protections within domains, see Chapter 5, Organizing Your Network into Domains, in this guide.
An important use of servers on most networks is to share files and directories among network users. The Advanced Server provides high performance, reliability, and security for file sharing.
The Advanced Server enables the sharing of local OpenVMS files to network users. You can use discretionary access controls and Advanced Server security on each file and directory to specify the groups and users that can access files, to define the levels of access that each group or user is permitted, and to control auditing. Additional security is provided by file ownership and OpenVMS file and directory protections.
You can set up printers connected to the OpenVMS system for network access by creating print shares for OpenVMS print queues defined for the printers. Printers are accessible to local OpenVMS users and network users. Beginning with Version 7.3 of the Advanced Server for OpenVMS, the server can be configured to enable management of its network printers from a Windows NT Server or workstation. You add a printer and make it available to the network by using Windows NT print services. For more details, see Section 7.4, Managing Print Shares, Print Queues, and Print Jobs. By default, the ADMINISTER command-line interface is used to manage printers. PATHWORKS for OpenVMS (Advanced Server) servers allow printer management from the ADMINISTER interface only.
You can use logon scripts to configure MS-DOS and Windows workstation user environments by making network connections and starting applications.
You can create user profiles to make workstation computers easier to use and to control workstation access to network resources.
For more information about using logon scripts and user profiles, see Chapter 2, Domains and Trusts, in this guide.
The Advanced Server provides event logging and the ability to monitor network activity and track computer usage.
You can display servers and see which resources they are sharing. You can display the users currently connected to any network server and see which files are open, log and display security auditing entries, keep sophisticated error logs, and specify that alerts be sent to administrators when certain events occur.
For information on how to monitor and track network activity, see your Server Administrator's Guide.
The Advanced Server can act as a Master Browser in a Windows NT network.
The installation process includes a configuration procedure (PWRK$CONFIG) that you use to set up your initial configuration. You can make additional adjustments to the configuration after running the configuration procedure:
Advanced Server offers license management for both client-based and server-based licenses.
To connect to the Advanced Server, clients must be properly licensed. The Advanced Server licensing subsystem keeps track of the licensing database and validates client licenses when clients attempt their initial connection to the server. The Advanced Server licensing subsystem includes the following basic components, which are automatically installed with the Advanced Server software:
Using the Advanced Server management interfaces, you can remotely manage other servers in the domain. You can remotely manage the following kinds of servers:
You can use the ADMINISTER command-line interface to manage servers, services, and domains. (The functionality for managing PATHWORKS V5 for OpenVMS (LAN Manager) and LAN Manager V2.2 servers is limited.)
For information on how to manage remote servers, see your Server Administrator's Guide.
You may install Advanced Server for OpenVMS on a system that was previously running PATHWORKS V6 for OpenVMS (Advanced Server). User, share, and security information in the Security Accounts Manager (SAM) database are automatically upgraded when you configure the Advanced Server.
If the system is running a server version previous to PATHWORKS V6.0C for OpenVMS (Advanced Server), then before you install the Advanced Server for OpenVMS, you should:
HP recommends the following migration path for systems running the PATHWORKS V5 for OpenVMS (LAN Manager) file server on OpenVMS Alpha Version 6.2 systems:
Refer to the appropriate Software Product Description (SPD) for information about the OpenVMS versions supported by each version of PATHWORKS for OpenVMS and Advanced Server for OpenVMS.
If you are running a version of PATHWORKS prior to V5, you must first upgrade to PATHWORKS V5 for OpenVMS (LAN Manager), and then upgrade to PATHWORKS V6 for OpenVMS (Advanced Server) before proceeding with the installation of your latest Advanced Server product.
When you install PATHWORKS V6 for OpenVMS (Advanced Server), the Upgrade utility is automatically included with it. You can use the Upgrade utility to upgrade the users, groups, shares, and security of a PATHWORKS V5 for OpenVMS (LAN Manager) server. If you want to continue running the PATHWORKS LAN Manager server while performing the upgrade, you must install the Upgrade utility separately before installing the PATHWORKS V6 for OpenVMS (Advanced Server).
For information on how to upgrade PATHWORKS LAN Manager servers to PATHWORKS V6 for OpenVMS (Advanced Server), see the Compaq PATHWORKS for OpenVMS Server Migration Guide. For information on installing the Upgrade utility, see the Compaq PATHWORKS for OpenVMS (Advanced Server) Server Installation and Configuration Guide.
The Advanced Server provides event logs and an audit trail. These resources let you track and manage server events and performance and troubleshoot problems. You can monitor and log events on any Advanced Server.
For more information on solving problems with the Advanced Server, see your Server Administrator's Guide.
The Advanced Server provides an administrative model for managing a large network efficiently. This model lets you manage and track the actions of users while allowing them to access the resources they need. Central to the idea of security in the Advanced Server is the concept that every resource and action is protected by discretionary access control. Discretionary access control allows you to permit some users to access a resource or perform an action while preventing other users from doing so.
Conventional OpenVMS file systems support simple file and directory protections --- read, write, delete, and execute --- for four categories of users: owners, members of the file owner's group, system administrators, and all others. The Advanced Server allows you to grant or deny users and groups a wide set of permissions; these permissions can work in concert with the standard OpenVMS file system protections. In addition, the Advanced Server allows you to apply a number of user:permission or group:permission pairs to any file, directory, or resource. You can set different permissions on different files in the same directory.
The basic administrative unit of Advanced Server is the domain. A domain is a collection of computers that share a common domain security accounts database (also called the domain's Security Accounts Manager (SAM) database or security database) and security policy. All of the Advanced Servers in a domain use the same set of user accounts. As a result, you need to enter information for a user account only once to allow all servers in the domain to recognize the user.
Trust relationships are links between domains. In a trust relationship, a user with an account in one domain can access resources provided by another domain. This feature is called pass-through authentication. If the domains and trust relationships on your network are well planned, all your Advanced Server computers can recognize every authorized user, so a user needs to log in only once to access any required resource on the network.
Grouping computers into domains offers significant benefits to network administrators and users. The first and most important benefit is that servers in a domain form a single administrative unit that can share security and user account information. Every domain has one database, referred to as the security accounts database or the Security Account Manager (SAM) database, that contains user and group accounts and security policy settings. Every server in the domain (except member servers) can maintain a copy of this database. One server, designated as the primary domain controller (PDC), maintains the master copy of this database. The master copy is synchronized with the copies of the database that are stored on the backup domain controllers (BDCs) in the domain. The primary domain controller replicates its databases to the backup domain controllers. Normally, synchronization occurs automatically at regular intervals. Administrators can also synchronize them manually. For more information, see your Server Administrator's Guide.
By extending the administrative unit from a single computer to an entire domain in this way, the Advanced Server saves administrators and users time and effort. For example, administrators need to manage only one account for each user, and each user needs to use only one account. The user account information is replicated to the security account databases maintained domain-wide. Figure 2-1 shows four domains set up as basic administrative units on a network.
Figure 2-1 Grouping Computers into Domains

The second benefit of domains is user convenience. When users browse the network for available resources, they see the network grouped into domains instead of viewing all the individual servers on the network. This implementation of domains is similar to the use of workgroups in Microsoft Windows for Workgroups. Advanced Server domains are compatible with workgroups in the Windows for Workgroups platform.
For more information about Windows for Workgroups, see Section 2.6.4, Windows for Workgroups Computers, in this guide.
Do not confuse Advanced Server domains with TCP/IP network protocol domains. A TCP/IP domain describes part of the TCP/IP Internet and is not related to Advanced Server domains. |
You can provide a user with access to resources in a second domain without creating and maintaining a separate user account in the second domain, and without granting hard-to-maintain individual permissions directly to the person. A user can access resources in other domains as easily as those in the user's own domain.
To allow a user access to resources in a domain where the user has no user account, you can:
The text and examples that follow will clarify several new terms introduced here, such as share, global group, and local group. For definitions of new terms, you can also see the Glossary in this guide.
Trust relationships between domains enable user accounts to be used in domains other than the ones in which they reside. Trust relationships make administration easier because you create user accounts only once on your network. Then, you can give a user account access to any computer on the network, not only to the computers in one domain.
When you establish a one-way trust relationship between domains, one domain (the trusting domain) trusts the other (the trusted domain). Figure 2-2 shows a one-way trust relationship in which the Production domain trusts the Sales domain. Users from the Sales domain can access resources in the Production domain even though they do not have accounts in the Production domain.
Sales, however, does not trust Production; therefore, resources from Sales cannot be used by users in the Production domain.
Figure 2-2 A One-Way Trust Relationship

Establishing this one-way trust relationship requires administrative access to both domains and a password. For example:
Subsequently, the trusting domain Production recognizes all user and global group accounts from the trusted domain Sales. These accounts can be used anywhere in the trusting domain: they can log on at workstations, reside in local groups, or be given access to resources in the trusting domain. For more information on establishing a one-way trust, see your Server Administrator's Guide.
A trust relationship can be one-way or two-way. A two-way trust relationship is a pair of one-way relationships in which each domain trusts the other.
In Figure 2-3, the Finance and Shipping domains trust each other; therefore, accounts in each of these domains can be used in the other. Users in the Finance domain can access resources in the Shipping domain, and users in the Shipping domain can access resources in the Finance domain.
Figure 2-3 A Two-Way Trust Relationship
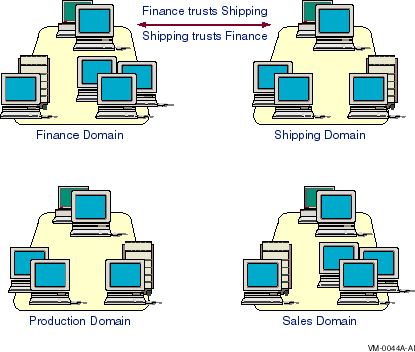
For more information on establishing a two-way trust relationship, see your Server Administrator's Guide.
Trust relationships among domains are not transitive. Although, as shown in Figure 2-4, Production trusts Sales and Sales trusts Finance, it does not follow that Production trusts Finance automatically. If Production needs to trust Finance and allow Finance accounts to be used in the Production domain, you must establish an explicit trust relationship between Production and Finance.
Figure 2-4 A Nontransitive Trust Relationship

Remember that you must take steps in each domain to define trusted and trusting domains, as discussed in the preceding sections and, in more detail, in your Server Administrator's Guide.
The minimum requirement for an Advanced Server domain is one server running either Advanced Server (OpenVMS or UNIX) or Windows NT Server software. This computer serves as the primary domain controller (PDC) and stores the master copy of the domain's security accounts database. A domain can contain only one PDC. As discussed in Section 2.5.3, Member Server, Windows 2000 and Windows 2003 domains are composed differently. The Advanced Server can function in native-mode (pure) Windows 2000 domains and Windows 2003 domains as a member server, or in mixed-mode Windows 2000 domains and Windows 2003 interim domains as a backup domain controller (BDC) or member server.
A domain can include, as BDCs, other servers running Advanced Server (OpenVMS or UNIX), Windows NT Server, or LAN Manager V2.x software; it can also include Advanced Server, Windows NT Server, and LAN Manager V2.x servers as standalone or member servers. (The Advanced Server for OpenVMS can participate in Windows 2000 and Windows 2003 domains. For more information, see Section 2.5.2, Backup Domain Controller, and Section 2.5.3, Member Server.)
The clients in a domain can include Windows NT workstations; Windows 2000 and Windows XP workstations. The following sections discuss individual domain components in detail.
The following pertains to Advanced Servers operating in an OpenVMS Cluster:
The primary domain controller of an Advanced Server domain must be a server running either Advanced Server or Windows NT Server software. Every change made to a domain's user and group database is made to the database of the primary domain controller.
To change the user database when managing an Advanced Server with the ADMINISTER command, you specify only the name of the domain to which the change applies; you do not need to specify the server name. The Advanced Server makes the change automatically to the database of the primary domain controller. For more information on modifying the user database, see the ADD USER and MODIFY USER entry in the HP Advanced Server for OpenVMS Commands Reference Manual or the ADMINISTER commands online help.
In a domain, except for the primary domain controller, every server running Advanced Server or Windows NT Server is a backup domain controller or a member server. A backup domain controller stores a copy of the domain's security account database, which is automatically synchronized with the primary domain controller. You cannot change the user database on a backup domain controller.
Like the primary domain controller, a backup domain controller can process logon requests from users who want to log on to the domain. When the domain receives a request to log on, either the primary domain controller or any of the backup domain controllers can authenticate the logon attempt.
You should have at least one backup domain controller running Advanced Server or Windows NT Server in a domain. If the primary domain controller becomes unavailable, a backup domain controller can be promoted to primary domain controller and the domain can continue to function normally. Having multiple servers also distributes logon request processing; this is especially useful in domains with many user accounts.
In domains with multiple computers running Advanced Server, one acts as the primary domain controller and the other computers are designated as backup domain controllers or member servers. In domains with WAN configurations (with server computers at different locations), each site should have at least one backup domain controller running Advanced Server or Windows NT Server to permit logon validation if access to the primary domain controller becomes unavailable.
Note that as a BDC, the Advanced Server can partipate in Windows 2000 mixed-mode and Windows 2003 interim domains. To participate in a native-mode Windows 2000 domain or in a Windows 2003 domain, the Advanced Server must be configured as a member server, as described below.
| Previous | Next | Contents | Index |