Software > OpenVMS Systems > Documentation > 731final > 6663 HP OpenVMS Systems Documentation |
HP DECwindows Motif
|
| Previous | Contents | Index |
To enable Magic Cookie and grant one or more clients presenting a valid magic cookie access to your workstation display:
To disable Magic Cookie, deselect the Magic Cookie option and click OK or Apply.
To prevent other users from accessing the current session using the current cookie value, click on the Create Cookie button. The new cookie value is added to your default X authority file.
Any client applications that are connected to the X server when a new cookie is generated will remain connected. Authentication occurs only when initially connecting to the X server. |
Prerequisites
In order to enable Kerberos, you or your system administrator must have first performed the following on the server system:
To enable Kerberos, and grant one or more valid Kerberos principals access to your workstation display:
To disable Kerberos, deselect the Kerberos option, remove all principals from the list, and click OK or Apply.
To prevent one or more principals from accessing your session, first click on the name(s) you want to remove. Then click on the Remove button. Finally, click on OK or Apply. The principal will no longer have authorized access to your workstation.
To prevent all principals from accessing your session, click on the Revoke Ticket button, and click OK or Apply.
When a client application connects to an X server, the server determines which authentication protocol to use by accessing the current X Authority file. The X Authority file identifies the protocol to use based on the workstation to which the client is connecting. You can make changes to the X authority file using the Security Options dialog box or by directly using the X authority file, as described in Section 1.2.2.
To specify what access control scheme client applications on this workstation follow when connecting to an X server:
Changes to client access control settings impact the contents of the default X authority file entries (local and DECnet) for the current user only, and do not impact any other access control settings in place on the system. |
Using the SECURITY extension (described in Section 3.5.1.6), you can choose to manually generate authorization keys using xauth or the SET DISPLAY/GENERATE command. This allows you to specify one of the following additional attributes to apply to a server connection:
Client applications that have not been coded to allow for their use over an untrusted connection may behave unexpectedly. See the specification for the SECURITY extension from X.Org for a description of the limitations of an untrusted connection. |
To enable the SECURITY extension:
$ DECW$SERVER_EXTENSIONS == "SEC_XAG" |
The security policy file enables you to configure the server to allow certain actions (at the X atom level) to be performed over untrusted network connections. This file establishes one or more site policies that specify the set of allowable actions through a series of field definitions.
A sample file has been provided with DECwindows Motif and is located in DECW$EXAMPLES:DECW$SECURITY_POLICY.TXT. Use this file as a template when creating a policy file. Security policies are described in the Security Extension Specification Version 7.1 published by X.Org. Refer to this specification for details regarding the use and definition of security policies.
To establish a security policy file on a DECwindows Motif system, do the following:
Although LBX reduces data flow between systems, it is not recommended for a LAN-only environment. While it does reduce overall traffic flow, this comes at a cost of increased processing requirements. This generally results in a slight decrease in performance in a LAN-only environment. |
The components of the LBX implementation in DECwindows Motif (see Figure 2-1) are as follows:
Figure 2-1 LBX Components
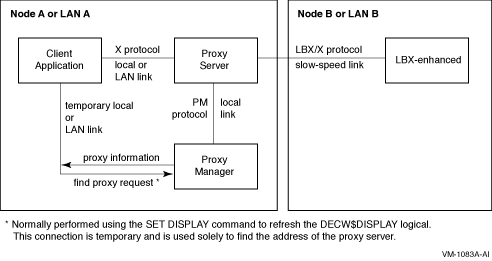
Because the communication between the client and the proxy server uses the unoptimized X protocol, the client and the proxy server should always be on the same node or on the same LAN. |
Proxy servers can be categorized as one of the following according to their relation to the proxy manager:
Note the DECwindows Motif LBX proxy server is currently supported only as a managed or standalone configuration.
How you start an LBX proxy server determines the proxy server's type and how a client accesses the proxy server.
Before you start an LBX proxy server, ensure that the proxy server is properly authorized to connect to the X server. For more information about authentication in an LBX proxy environment, see Section 2.7.3. |
To start a managed LBX proxy server, place the following LBX service entry in the proxy manager's configuration file (see Section 2.7.2.1).
LBX MANAGED COMMAND SYS$MANAGER:DECW$LBXPROXY_SUB ["qualifiers"] |
After the proxy manager is configured, no specific action is required to start the proxy server; the proxy manager starts the server when the manager receives the first client request.
You can start standalone LBX proxy servers either in the current process or as a detached process. To start a standalone proxy server in the current process, use the LBXPROXY command.
LBXPROXY [qualifiers] |
For example, to start a proxy server in the current process, assign it server number 50, and have the server act as a proxy for the X server on node remote1.cmp.com, use the following command:
$ LBXPROXY /DISPLAY="REMOTE1.CMP.COM:0"/SERVER=50/FIXED_SERVER |
To start a proxy server as a detached process, use the DECW$LBXPROXY command procedure.
@SYS$MANAGER:DECW$LBXPROXY ["lbxproxy-qualifiers"] ["run-qualifiers"] |
For example, to start a proxy server as a detached process, assign it server number of 50, and have the server act as a proxy for the X server on node remote1.cmp.com, use the following command:
$ @SYS$MANAGER:DECW$LBXPROXY "/DISPLAY=""REMOTE1.CMP.COM:0""" + - _$ "/SERVER=50/FIXED_SERVER" |
Use the run-qualifiers parameter to pass any qualifiers to the RUN command used to invoke the LBXPROXY image. One use of this parameter might be to override the default LBXPROXY process characteristics or any values set by the logicals provided to modify these defaults.
To start an LBX proxy server as a detached process requires the DETACH privilege or available maximum detached process quota. To modify the process quotas for a detached process requires the DETACH privilege. |
Modifying the Default LBXPROXY Process Characteristics
Table 2-2 lists the logicals that are provided to override the default LBXPROXY process characteristics specified on the RUN command generated by SYS$MANAGER:DECW$LBXPROXY.
| Logical | RUN Command Qualifier |
|---|---|
| DECW$LBX_AST_LIMIT | /AST_LIMIT |
| DECW$LBX_BUFFER_LIMIT | /BUFFER_LIMIT |
| DECW$LBX_DUMP | /DUMP |
| DECW$LBX_ENQUEUE_LIMIT | /ENQUEUE_LIMIT |
| DECW$LBX_EXTENT | /EXTENT |
| DECW$LBX_FILE_LIMIT | /FILE_LIMIT |
| DECW$LBX_IO_BUFFERED | /IO_BUFFERED |
| DECW$LBX_IO_DIRECT | /IO_DIRECT |
| DECW$LBX_LOG | /ERROR |
| DECW$LBX_MAXIMUM_WORKING_SET | /MAXIMUM_WORKING_SET |
| DECW$LBX_PAGE_FILE | /PAGE_FILE |
| DECW$LBX_PRIORITY | /PRIORITY |
| DECW$LBX_PROCESS_NAME | /PROCESS_NAME |
| DECW$LBX_QUEUE_LIMIT | /QUEUE_LIMIT |
| DECW$LBX_WORKING_SET | /WORKING_SET |
Enter LBXPROXY command qualifiers in the same manner as you would for any other DCL command. For managed servers, specify these qualifiers on the LBX service line in the proxy manager's configuration file.
Specifies the file that the proxy server should use for atoms control. The file SYS$MANAGER:DECW$ATOMCONTROL.TEMPLATE contains an example of an atom control file. This qualifier cannot be specified if the NOATOMS or NOLBX option is specified for the /OPTION qualifier.
The default is /ATOMS=SYS$MANAGER:DECW$ATOMCONTROL.DAT. However, effectively the default is not to use atom control because the installation process does not convert the SYS$MANAGER:DECW$ATOMCONTROL.TEMPLATE file to the SYS$MANAGER:DECW$ATOMCONTROL.DAT file.
At startup, the LBX proxy server "pre-interns" the atoms specified in the atom control file. The atom control file also controls when the proxy server should delay sending data to the X server. This is done by specifying the following:
The format of the atom control file is documented in the SYS$MANAGER:DECW$ATOMCONTROL.TEMPLATE file.
/CHEAT={ERRORS | EVENTS | NONE}
Specifies the level of cheating allowed on the X protocol for the sake of improved performance. The X protocol guarantees to the requesting party that all corresponding replies, events, or errors are returned to the requester in the same order as the original requests. The ERRORS option allows the proxy server to violate the X protocol with respect to errors. The EVENTS option allows the proxy server to violate the X protocol with respect to errors and events. The NONE option specifies that no protocol cheating is allowed.
The default is /CHEAT=NONE.
Some X applications may rely upon the correct ordering of events and errors. Enabling cheating may cause these applications to fail. Use this option at your own risk. |
/DISPLAY={"network-address" | logical-name |
device-name}
Specifies a network address, logical name, or device name that references the X server to which the proxy server should connect. A network address must be in the following form:
"[transport\][node][:]:display[.screen]" |
This option is ignored for managed proxy servers.
The default is /DISPLAY=DECW$DISPLAY.
/FIXED_SERVER
/NOFIXED_SERVER
Specifies that the proxy server should fail to start if the server number specified by the /SERVER qualifier is not available. See /SERVER qualifier for more information about server numbers. This option is useful for starting standalone servers as detached processes. In this case, the proxy server has no method to return the selected server number. This option is ignored for managed proxy servers.
The default is /NOFIXED_SERVER.
/MAXSERVER=value
Specifies the maximum number of X servers to which this proxy server can connect. This option is ignored for standalone servers. Specify a value from 1 to 63.
/MOTION=value
Specifies the maximum number of pointer motion events that are allowed to remain unanswered between the proxy server and the X server. Specify a value from 1 to 32767.
/ONERROR={RECONNECT | TERMINATE}
Specifies the action taken when the proxy server encounters an internal error. This usually occurs when the proxy server looses its connection to the X server.
| RECONNECT | Specifies that the proxy server should clean up its internal state information and await further requests. If the proxy server is a standalone server, this option also specifies that the proxy server should reconnect to the X server. For managed proxy servers with multiple connected X servers, the proxy server will try to reconnect each server connection when it fails. |
| TERMINATE | Specifies that the proxy server should exit. For managed proxy servers with multiple connected X servers, the proxy server will terminate only if all X server connections fail. |
The default is /ONERROR=TERMINATE.
/ONEXIT={NOACTION | RESET | TERMINATE}
Specifies the action taken by this proxy server when the last client exits.
| NOACTION | Specifies that the proxy server should continue running. |
| RESET | Specifies that the proxy server should clean up its internal state information and await further requests. If the proxy server is a standalone server, this option also specifies that the proxy server should reconnect to the X server. |
| TERMINATE | Specifies that the proxy server should exit. |
The default is /ONEXIT=NOACTION.
/OPTIONS=(option-list)
Specifies the optimizations to use for this proxy server. With the exception of ALL and NONE, each option has a NOoption form that disables the option. To enable a small number of options, use a combination of the NONE and the desired options. For example, /OPTIONS=(NONE,IMAGE) suppresses all optimization with the exception of image compression. To disable a small number of options, use a combination of the ALL and the undesired options. For example, /OPTIONS=(ALL,NOIMAGE,NOGRAPHICS) suppresses image and graphics optimization.
| ALL | Enables all optimizations. The ALL and NONE options are mutually exclusive. |
| NONE | Disables all optimizations. The ALL and NONE options are mutually exclusive. |
| [NO]ATOMS | Enables [disables] reading of the atoms control file. The NOATOMS option is mutually exclusive with the /ATOMS qualifier. |
| [NO]GRABCMAP | Enables [disables] color map grabbing. |
| [NO]COMP | Enables [disables] stream compression. |
| [NO]DELTA | Enables [disables] delta request substitutions. |
| [NO]GRAPHICS | Enables [disables] reencoding of graphics requests (other than image-related requests). |
| [NO]IMAGE | Enables [disables] image compression. |
| [NO]INTERNSC | Enables [disables] short circuiting of InternAtom requests. |
| [NO]LBX | Enables [disables] all LBX optimizations (equivalent to [NO]ATOMS, [NO]GRABCMAP, [NO]GRAPHICS, [NO]IMAGE, [NO]INTERNSC, and [NO]WINATTR). The [NO]LBX option is mutually exclusive with any of the options controlled by [NO]LBX. The NOLBX option is mutually exclusive with the /ATOMS qualifier. |
| [NO]RGB | Enables [disables] color name to RGB mapping in the server. The NORGB option is mutually exclusive with the /RGB qualifier. |
| [NO]SQUISH | Enables [disables] squishing of X events. |
| [NO]TAGS | Enables [disables] use of tags. |
| [NO]WINATTR | Enables [disables] GetWindowAttributes/GetGeometry grouping into one round trip. |
| [NO]ZEROPAD | Enables [disables] zeroing out unused pad bytes in X requests, replies, and events. |
| Previous | Next | Contents | Index |