Software > OpenVMS Systems > Documentation > 82final > 6543 HP OpenVMS Systems |
HP Advanced Server for OpenVMS
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Previous | Contents | Index |
The Alerter Service Parameters key is:
SYSTEM\CurrentControlSet\Services\Alerter\Parameters |
Table A-11, Alerter Service Values, lists the values that may be stored in the Alerter Service Parameters key.
| Value | Description | |
|---|---|---|
| AlertNames | Specifies a list of the Advanced Server user accounts to receive administrative alerts. To receive alerts, a client workstation must be running the Messenger service. The Messenger service is not supported on HP OpenVMS servers. | |
| Valid Data: | Unlimited | |
| Default Data: | Administrator | |
| LANMAN.INI Section: | SERVER | |
| LANMAN.INI Keyword: | alertnames | |
| Parameter Type: | Dynamic | |
| Data Type: | Expanded string | |
The Application Event Log key is:
SYSTEM\CurrentControlSet\Services\EventLog\Application |
Table A-12, Application Event Log Values, lists the values that you can store in the Application Event Log key.
| Value | Description | |
|---|---|---|
| MaxSize | Specifies the maximum size, in kilobytes, of the Application event log file. | |
| Valid Data: |
Minimum: 1024
Maxmimum: unlimited |
|
| Default Data: | 524288 | |
| LANMAN.INI Section: | SERVER | |
| LANMAN.INI Keyword: | maxapplog | |
| Parameter Type: | Static | |
| Data Type: | Integer | |
| Retention | Specifies the amount of time, in seconds, to maintain the Application event log. | |
| Valid Data: |
Minimum: 0
Maximum: unlimited |
|
| Default Data: | 604800 | |
| Parameter Type: | Static | |
| Data Type: | Integer | |
The Security Event Log key is:
SYSTEM\CurrentControlSet\Services\EventLog\Security |
Table A-13, Security Event Log Values, lists the values that may be stored in the Security Event Log key.
| Value | Description | |
|---|---|---|
| MaxSize | Specifies the maximum size, in kilobytes, of the Security event log file. | |
| Valid Data: |
Minimum: 1024
Maximum: unlimited |
|
| Default Data: | 524288 | |
| LANMAN.INI Section: | SERVER | |
| LANMAN.INI Keyword: | maxauditlog | |
| Parameter Type: | Static | |
| Data Type: | Integer | |
| Retention | Specifies the amount of time, in seconds, to maintain the Security event log. | |
| Valid Data: |
Minimum: 0
Maximum: unlimited |
|
| Default Data: | 604800 | |
| Parameter Type: | Static | |
| Data Type: | Integer | |
The System Event Log key is:
SYSTEM\CurrentControlSet\Services\EventLog\System |
Table A-14, System Event Log Values lists the values that may be stored in the System Event Log key.
| Value | Description | |
|---|---|---|
| MaxSize | Specifies the maximum size, in kilobytes, of the system event log file. | |
| Valid Data: |
Minimum: 1024
Maximum: unlimited |
|
| Default Data: | 524288 | |
| LANMAN.INI Section: | SYSTEM | |
| LANMAN.INI Keyword: | maxerrlog | |
| Parameter Type: | Static | |
| Data Type: | Integer | |
| Retention | Specifies the amount of time, in seconds, to maintain the system event log. | |
| Valid Data: |
Minimum: 0
Maximum: unlimited |
|
| Default Data: | 604800 | |
| Parameter Type: | Static | |
| Data Type: | Integer | |
The User Service Parameters key is:
SYSTEM\CurrentControlSet\Services\AdvancedServer\UserServiceParameters |
Table A-15, User Service Parameter Values, lists the values that may be stored in the User Service Parameters key.
| Value | Description | |
|---|---|---|
| HostmapUseVMSNames | Checks to see if the network user name matches an OpenVMS user account name when the user logs onto the domain. Explicit host mapping is checked and used first. If host mapping has not been specified, the software searches for a matching OpenVMS user name. | |
| Valid Data: | YES or NO | |
| Default Data: | YES | |
| LANMAN.INI Section: | VMSSERVER | |
| LANMAN.INI Keyword: | hostmapusevmsnames | |
| Parameter Type: | Static | |
| Data Type: | String | |
| HostmapDomains | Specifies domain names for user accounts in trusted domains, allowing the Advanced Server to perform external authentication on a network user name located in the domains. Checks to see if the user's domain name matches one of the domains listed, where the network user name matches an OpenVMS user account name. | |
| Valid Data: |
domainname,
domainname,... (List of domains used for OpenVMS host mapping.) |
|
| Default Data: | None. The server's domain name is assumed. | |
| LANMAN.INI Section: | VMSSERVER | |
| LANMAN.INI Keyword: | hostmapdomains | |
| Parameter Type: | Static | |
| Data Type: | Multistring | |
| HostmapDefault | The data associated with this value is used when no other host mapping definitions apply. | |
| Valid Data: | ADMINISTRATOR, DEFAULT, GUEST, or REJECT | |
| Default Data: | DEFAULT | |
| LANMAN.INI Section: | VMSSERVER | |
| LANMAN.INI Keyword: | hostmapdefault | |
| Parameter Type: | Static | |
| Data Type: | String | |
With its open architecture, the Advanced Server software can operate over several popular protocols simultaneously, including:
This appendix provides information about the following topics:
Before you explore the specific drivers and protocols supported by the Advanced Server, you should understand both the OSI Reference Model and the purpose of network interface card drivers. If you already understand these topics, you can skip to Choosing a Network Protocol, which includes an overview and description of each protocol that interoperates with the Advanced Server.
In 1978 the International Organization for Standardization (ISO) developed a model for computer networking called the Open Systems Interconnection (OSI) Reference Model. The model describes the flow of data in a computer network---from the physical connections of the network to the applications used by the end user.
The OSI Reference Model is an idealized version of networking; few systems follow it exactly. However, the model is useful for discussion and comparison of networks.
The OSI Reference Model includes seven layers, as shown in Figure B-1, OSI Reference Model. Each of the layers is responsible for a specific and discrete aspect of networking.
Figure B-1 OSI Reference Model
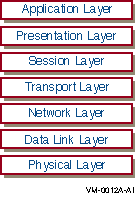
The following list describes each OSI Reference Model layer in detail:
Figure B-2 Transport Protocol
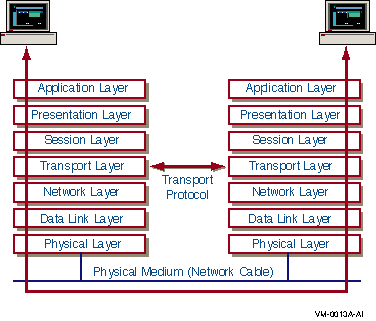
A network adapter card, also called a network interface card or a network interface controller (NIC), is an adapter board installed in a computer to let it function on a network. The network adapter card provides ports to which the network cable can connect physically. The card physically transmits data from the computer to the network cable, and back.
Every network computer must have a network adapter card driver, a software driver that controls the network card. Every network adapter card driver is configured to run with a certain type of network card.
When choosing network adapter cards, you first must choose cards that support your network's architecture (such as Ethernet or Token Ring) and cabling media (such as Thinnet or twisted pair). You also should consider the tradeoffs of performance and cost.
Performance for network adapter cards depends mostly on bus width and onboard memory. The best performance is achieved when the bus width of the card closely matches the internal bus width of the computer. Onboard memory enables a card to buffer frames going to and from the network. A card with the most memory is not always the best choice. At some point, diminishing returns and the maximum speed of other network components limit the performance gains of onboard memory.
When you consider the cost of network cards, factor in the cost of buying spare cards to replace the ones that fail. You should also ensure that your network hardware budget allows for cable, hubs, repeaters, routers, and other hardware, as well as the labor costs associated with installing them.
Before you decide on a type of network card, make sure that the OpenVMS operating system you are using supports it. Also, make sure the vendor can support your business needs. If you are working with a reseller, check that the reseller has good communication with the card manufacturer.
In addition to the network card and the network card driver, a network computer must have a protocol driver, also called a transport protocol or a protocol. The protocol driver works between the upper-level network software---such as the workstation and server---and the network adapter card. The protocol packages the data that are sent over the network in a way that the computer on the receiving end will understand.
The process of associating a protocol driver with the network adapter card with which it will work and establishing a communication channel between the two is called binding.
For two computers to communicate on a network, they must use identical protocols. In the case where computers are configured to use multiple protocols, they need to have only one protocol in common to communicate. For example, a server that uses both NetBEUI and TCP/IP can communicate both with workstations that use only NetBEUI and with workstations that use only TCP/IP.
The Advanced Server allows connections from the transports and protocols shown in Table B-1, Supported Transports and Protocols.
| Protocol | Client Transport | Server Transport Component |
|---|---|---|
| TCP/IP | Internet | Product-specific |
| NetBEUI (with NETBIOS) | LAN Manager | LAN Manager |
| DECnet (proprietary) | DECnet | DECnet |
The remainder of this section provides an overview of each of these protocols with basic information about each protocol and its advantages and disadvantages.
TCP/IP was developed in the late 1970s as a result of a research project on network interconnection by the Department of Defense Advanced Research Projects Agency (known as ARPANet, the precursor to the Internet). TCP/IP is actually a suite of protocols that defines various interactions between computers sharing the protocol.
Since the PC began its rise in popularity, TCP/IP has become a standard protocol for support in the PC networking environment.
TCP/IP has a reputation as a difficult protocol to configure and manage. However, current implementations are making it easier. For example, in TCP/IP, the Dynamic Host Configuration Protocol (DHCP) provides server support and is one of the most important advances in PC networking. Without DHCP, system administrators had to manually assign the four-byte IP addresses to each computer. With DHCP enabled, a DHCP server can manage a range of IP addresses and assign one to each computer as it logs on to the network.
The principal advantage of TCP/IP is that it provides communication across interconnected networks with different operating systems and hardware architectures.
TCP/IP provides compatibility with the Internet, a collection of networks and gateways linking universities, corporations, government offices, and military installations worldwide.
Table B-2, TCP/IP Protocol, summarizes the advantages and disadvantages of using the TCP/IP protocol.
| Advantages | Disadvantages |
|---|---|
| Provides connectivity across different operating systems and hardware platforms. | Slower than NetBEUI on small LANs. |
| Provides Internet connectivity. | Can be difficult to administer. |
| Provides routing support. | More overhead than NetBEUI. |
| Previous | Next | Contents | Index |